Using the Report Message option
The Report Message button allows you to easily report suspicious messages simultaneously to Microsoft and to the Minnesota State Information Security, Risk and Compliance Team. Users will no longer have to forward suspicious messages to phish@minnstate.edu. Implementation of this button will help the Minnesota State security team more rapidly and effectively identify dangerous attacks and automate the cleanup process.
Reporting a suspicious email is simple
1. While viewing the message, select the Report Message option from the Outlook ribbon.

2. Select the appropriate option, e.g. Junk, Phishing, etc.
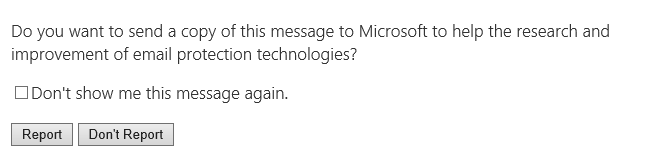
3. After you select Junk or Phishing you'll receive a message similar to the one below where you can choose to not show the message and then choose to report.
If you receive phishing or junk email in your inbox, please use the Report Message button to identify the message to help improve our email filters. If you are questioning if the email is phishing please reach out to your local Computer Help Center.
Junk mail, sometimes referred to as spam, is typically unsolicited, of a commercial nature (e.g. advertising) and usually sent in bulk. These messages may be treated similar to the way we would treat the garbage we receive from the post office and can simply be deleted. Some of the protections in Office365 help identify mail as junk and put them in your junk folder, so items already there do not need to be reported. Users are discouraged from even opening messages in their junk folder. If a user is absolutely certain that a message has been incorrectly classified as Junk, they can: highlight the message, click on Report message, then select Not Junk to move the item back to their Inbox and help “tune” the Office365 Junk filters.
While they can be similar to spam, phishing messages also carry a heavy dose of malicious intent -- attempting to collect information to be used for illicit purposes such as potential identity theft, embarrassment, ruined reputations and harassment, disrupted operations of accounts, compromise of brand integrity for businesses and loss of data, spread of malware, or theft of intellectual property.
Browse our Services Submit a Service Request Contact Us